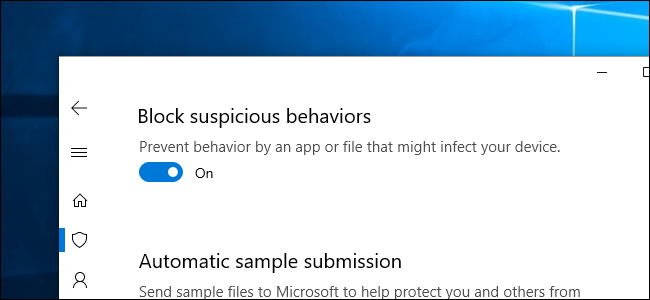
The Redstone 5 update of Windows 10 contains a new security feature named ‘Block Suspicious Behaviors’. This security aspect is intended to protect your device from suspicious behavior of any application and variety of threats.
This blog will let you know how to turn on or turn off the Block Suspicious Behaviors feature preventing any file or app to infect your device.
‘Block Suspicious Behavior’ is just a favorable name for ‘Windows Defender Exploit Guard attack surface reduction technology’. This security option was initially introduced in the Fall Creator Update which was only available for Windows 10 enterprise. But after Redstone 5 update, it can be accessed by everyone under Windows Security.
This security feature is disabled by default. You must be signed in as an administrator to enable ‘Block Suspicious Behaviors’.
Below are some suspicious actions that might occur due to malicious applications:
- Executable content from email client and webmail
- MS Office applications from creating child processes, executable content, inserting code into other processes
- JavaScript or VBScript from commencing downloaded executable content
- Implementation of potentially obscured scripts
- Win32 API calls from Office macro
- Credential abduction from the Windows local security authority subsystem (lsass.exe)
- Process creations generating from PSExec and WMI commands
- Executable on USB drives
All these suspicious activities are prevented by ‘Block Suspicious Behaviors’ features. An organization may personalize which rule it wants to utilize through group policy. However, for users’ PCs, a one-size-fits-all set of rules is recommended.
How to Enable ‘Block Suspicious Behaviors’ in Windows 10
Add an additional layer of security to your PC to avoid suspicious behaviors that may infect your device by following these steps:
Step 1: Go to ‘Setting’.
Step 2: Click on ‘Update & Security’.

Step 3: Select ‘Windows Defender’ from the right side pane and then click on ‘Open Windows Defender Security Center’.

Step 4: Select ‘Virus & threat protection’.
Step 5: Under ‘Virus & threat protection settings’, go to ‘Manage settings’ link.

Step 6: Turn on the toggle button to enable ‘Block Suspicious Behavior’.

Step 7: Confirm the UAC prompt by clicking on ‘Yes’.
Doing so will immediately enable the Block suspicious behavior. You can disable it using the same process if you change your mind later.
Block Suspicious Behaviors via Registry Editor
Step 1: Press Win and R keys together to open the run command. Write ‘regedit’ or ‘C:\Windows\regedit.exe’ and hit enter to open registry settings.
Step 2: Click ‘Yes’ when you come across an UAC prompt.
Step 3: Navigate to ‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Windows Defender Exploit Guard\ASR’
Step 4: Right-click the ‘ASR key’ and choose ‘Permissions’ in the right side pane.
Step 5: Go to ‘Advanced’ button and click on ‘Change’ link next to the Owner.
Step 6: Type ‘Administrators’ in the text field provided and click ‘Check Names’ button. Press ‘OK’.
Step 7: In ‘Advance Security Setting’ window, checkmark the option ‘Replace owner on subcontainers and objects’. Click ‘Apply’ followed by ‘OK’ to provide ownership of the key to administrator.
Step 8: Go back to ‘Permission’ dialog box, choose the ‘Administrator’ account and checkmark the ‘Full control’ box under ‘Allow’ column.
Step 9: On the right side pane of ‘ASR’ key, double-click the ‘EnableASRConsumers’ in the left-side pane.
Step 10: Put ‘Value data’ ‘1’ to enable the feature and ‘0’ to disable the feature.
Restart the system after enabling the ‘Block Suspicious Behaviors’.